What is CIBA
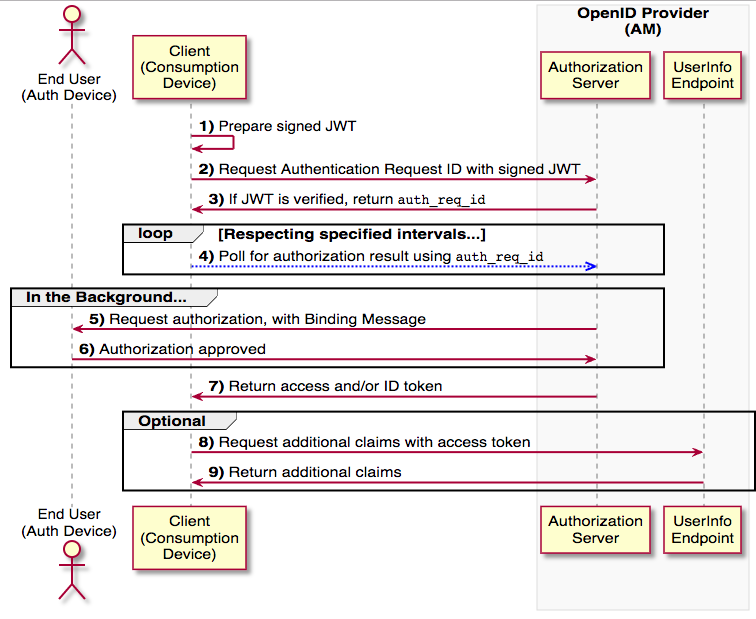
CIBA is an acronym for Client Initiated Backchannel Authentication and its based on OpenID Connect. CIBA allows a client application, known as a consumption device, to obtain authentication and consent from a user without requiring the user to interact with the client directly. Instead, the client application can initiate a backchannel request to the user's authentication device, such as a smartphone with an authenticator app installed, to authenticate the user and consent to the operation.
The Backchannel Request grant is used when performing CIBA. The following diagram demonstrates the Backchannel Request grant flow:
More information can be found in the following blog post
Integration
For CIBA integration the OpenID Provider (Audkenni) and the Client (Relying Party in OpenID connect flow) first need to exchange their endpoints, signing data and credentials which each other.
1. Information provided by the OpenID provider:
The endpoints of the OpenID Provider are static and can be found here (together with other information about the Audkenni provider). The most important endpoints are:
bc-authorize: https://idp.audkenni.is:443/sso/oauth2/realms/root/realms/audkenni/bc-authorize
token: https://idp.audkenni.is:443/sso/oauth2/realms/root/realms/audkenni/access_token
userinfo https://idp.audkenni.is:443/sso/oauth2/realms/root/realms/audkenni/userinfo
Next to that, the OpenID Provider will provide a client_id and a client_secret to the Client (Relying Party)
2. Information provided by the Client:
The Relying Party only needs to provide the information how he is going to sign the request JWT in order for to validate it. e.g. In case the clients signs the JWT with a private key the OpenID provider will need the public key. If the client uses a JSON web key then the OpenID provider would need the Public key of that web key
3. Setup
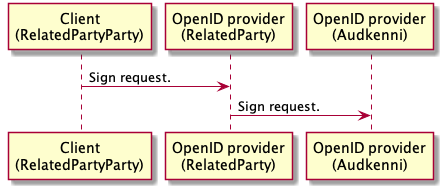
In some cases, the Client is also an OpenID provider that received a request from other Clients and relies on Audkenni for the actual signing. This scenario is seen in the picture below.
All information needed to let the user sign the message should be in the request JWT, as can be seen below:
{
"claims":
{
"login_hint": "8422263",
"scope": "openid profile signature RELATEDPARTY:clientname",
"acr_values": "sim-sign",
"iss": "clientid",
"aud": "https://idp.audkenni.is/oauth2/realms/root/realms/audkenni",
"exp": 238932499002,
"binding_message": "binding display message",
"binding_content": "binding content"
},
"key":"{{private_key}}",
"alg":"RS256"
}
The following parameters can be modified:
login_hint | In case the sim solution is used to sign the message this MUST contain the mobile number of the user |
scope | In case of a proxy scenario this should contain the name of the initial requesting party |
acr_values | This determines the method that is going to be used to sign the message. Valid values are sim_sign and nexus_sign |
binding_message | This is the message that the user will see when receiving the sign request |
binding_content | This is the actual content that will be signed |